Fault injection attacks exploit abnormal temperature, radiation, and other hardware parameters to disrupt systems-on-chip (SoCs), inducing errors that allow an attacker to access sensitive data or gain privileges. At the center of SoC security is the Secure Element (SE), conventionally verified through a post-silicon characterization, an approach that is not only costly, but that also produces variable results depending on the tester, tools, and other factors.
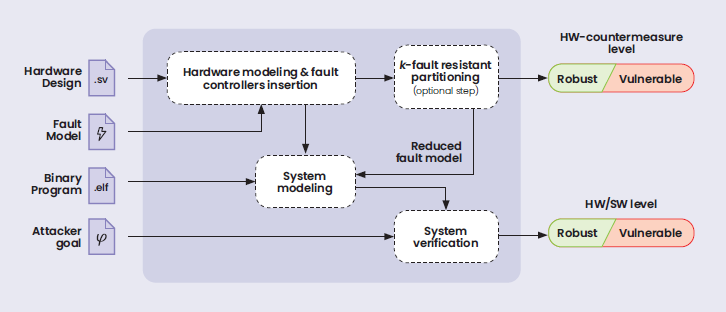
Pre-silicon analysis methods are needed to reduce security certification costs and turnaround times. The idea is to determine the extent to which the software and hardware countermeasures present can actually protect the SE. µArchiFI, developed by CEA-List, is a state-of-the-art pre-silicon analysis tool for assessing the robustness of SEs to fault injection attacks. To identify vulnerabilities or, on the contrary, formally prove that the system is robust, it uses a circuit description at Register Transfer Level (RTL), a fault model, a program, and an attack objective. Previously, µArchiFI only supported a limited fault model and around a hundred instructions—limitations that prevented the analysis of an SE’s boot code under a fault injection attack.
A method called k-Fault resistant Partitioning (k-FRP), developed in partnership with the Technical University of Graz (TU Graz), was added to our own analysis toolkit. The research led to the first-ever fault injection security analysis of OpenTitan, the first open-source SE developed by a consortium of digital systems and cybersecurity industry leaders.
The addition of k-FRP (which will ultimately become an optional step in the µArchiFI workflow) made it possible to:
Finally, the research demonstrated that the only vulnerability identified by k-FRP was not exploitable in the 2,500 instructions of the first stage of OpenTitan’s boot code. Prior to the development of this new approach, it was impossible to assess the security of this type of system, which is traditionally secured with redundant-hardware-type countermeasures.
Our pre-silicon analysis methodologies, integrating micro-architectural vulnerabilities, are central to the Forward project, part of the Campus Cyber tech transfer program (PTCC), and the TwinSec project, part of a special CEA program dedicated to bold, high-risk research, both of which started in late 2024. The goals are to compare such results to laboratory characterization data and to design a multi-level (physical, micro-architectural, and software) validation framework based on more realistic attacker models. Both projects address realistic multi-fault models and more complex processors.
The A-ranked Workshop on Cryptographic Hardware and Embedded Systems (CHES) is one of the leading international security conferences.
Several manufacturers and also the French Cybersecurity Agency (ANSSI) have shown interest in our analysis methods. For example, ANSSI is evaluating the use of formal methods as part of its security architecture analyses of the OpenTitan SE.
Links to our μArchiFI and k-fault resistant partitioning resistant Partitioning methodologies